Fixing upstream DNS issue with OpenWRT
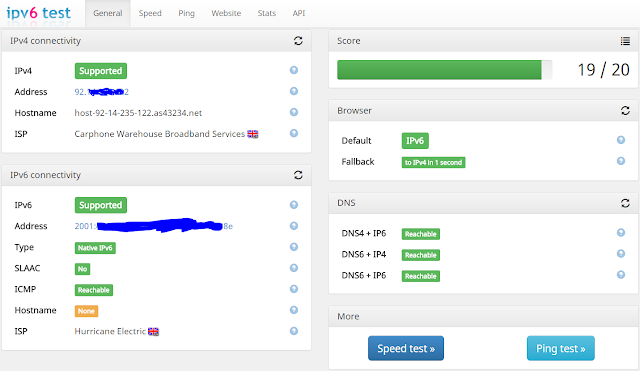
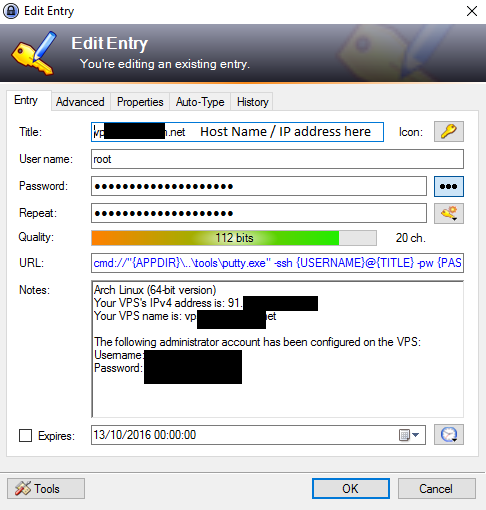
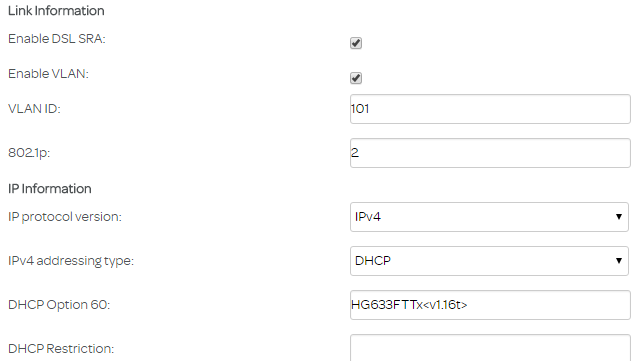
Problem: My Internet Provider provides crappy and "filtered" (monitored + augmented) DNS server withe their DHCP configured IPv4 connection. The intention is to use only Google Public DNS for resolution. It seems that all might be achieved by simply fixing /etc/config/network: Adding ### lines does: config interface 'wan' option ifname 'eth0.2' option proto 'dhcp' option peerdns '0' # do not use upstream DNS list dns '8.8.8.8' # use this particular DNS list dns '8.8.4.4' # use that particular DNS The above instantaneously bumped scoring up by 4 to 19/20. Most flagged issued were with DNS service. My ISP unfortunately provides slow IPv4. Switching to Google public DNS served, fixed also IPv6 connectivity. This also shows how far away is IPv6 adoption by my IPS.